Permissions API¶
Every data object in Backendless has its own access control list (ACL) - a matrix of operations and principals (application's users or roles). An intersection of an operation and a principal contains a permission which determines whether the principal has the right to execute the operation. These permission could be either grant or deny.
Backendless console provides an easy to understand way to see and manage these permissions. For example, the screenshot below demonstrates an ACL matrix for an object. Notice the intersection of a column for the Create operation and the AuthenticatedUser role. The cell contains a green checkmark icon representing that the permission is granted:
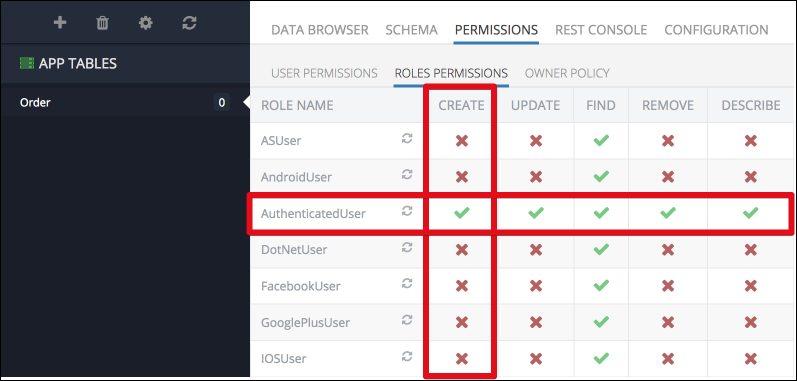
In addition to managing the ACL permissions with Backendless Console there is also Permissions API:
Methods¶
Methods described further are used for granting or denying access to a data object for a user, a role, all users, or all roles.
Use these methods for the Data operations (that is, to find, update, and remove the data) performed by DataPermission class, which is available in BackendlessAPI.Persistence namespace.
DataPermission.FIND.<method>to set a permission to find/retrieve a data objectDataPermission.UPDATE.<method>to set a permission to update a data objectDataPermission.REMOVE.<method>to set a permission to remove a data object
To grant access for a user¶
//Signatures
public void GrantForUser<T>( String userId, T dataObject )
public void GrantForUser<T>( String userId, T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.GrantForUser( userId, dataObject );
DataPermission.UPDATE.GrantForUser( userId, dataObject );
DataPermission.REMOVE.GrantForUser( userId, dataObject );
where:
| Argument | Description |
|---|---|
userId |
A user ID, for which you want to grant a permission. |
dataObject |
A data object for which you want to grant the permission. |
Codeless Reference¶
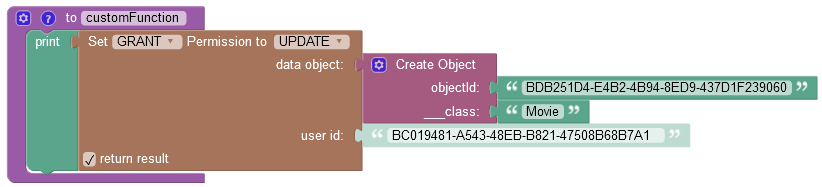
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to grant to a user. |
data object |
A data object for which you want to grant the permission. |
user id |
A user ID, for which you want to grant the permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To grant access for a user role¶
// Signatures
public void GrantForRole<T>( String roleName, T dataObject )
public void GrantForRole<T>( String roleName, T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.GrantForRole( roleName, dataObject );
DataPermission.UPDATE.GrantForRole( roleName, dataObject );
DataPermission.REMOVE.GrantForRole( roleName, dataObject );
where:
| Argument | Description |
|---|---|
rolename |
A role name, for which you want to grant a permission. |
dataObject |
A data object for which you want to grant the permission. |
Codeless Reference¶
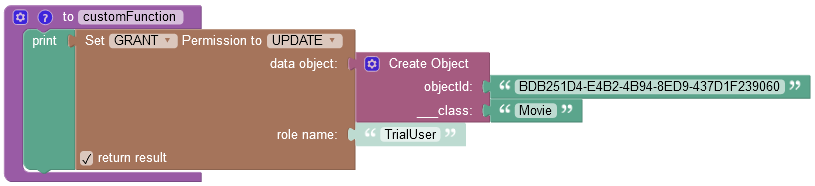
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to grant to a role. |
data object |
A data object for which you want to grant the permission. |
role name |
A role name, for which you want to grant a permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To grant access for all users¶
//Signatures
public void GrantForAllUsers<T>( T dataObject )
public void GrantForAllUsers<T>( T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.GrantForAllUsers( dataObject );
DataPermission.UPDATE.GrantForAllUsers( dataObject );
DataPermission.REMOVE.GrantForAllUsers( dataObject );
where:
| Argument | Description |
|---|---|
dataObject |
A data object for which you want to grant the permission. |
Codeless Reference¶
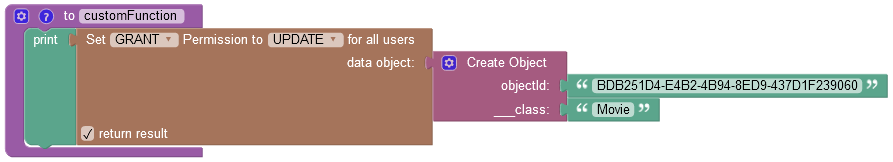
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to grant to all users. |
data object |
A data object for which you want to grant the permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To grant access for all roles¶
//Signatures
public void GrantForAllRoles<T>( T dataObject )
public void GrantForAllRoles<T>( T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.GrantForAllRoles( dataObject );
DataPermission.UPDATE.GrantForAllRoles( dataObject );
DataPermission.REMOVE.GrantForAllRoles( dataObject );
where:
| Argument | Description |
|---|---|
dataObject |
A data object for which you want to grant the permission. |
Codeless Reference¶
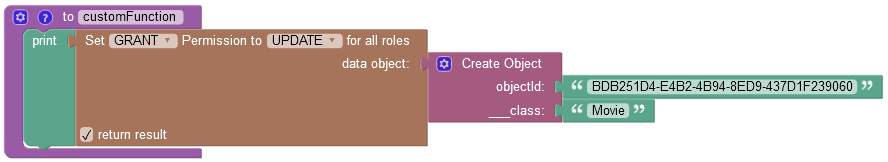
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to grant to all roles. |
data object |
A data object for which you want to grant the permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To deny access for a user¶
//Signatures
public void DenyForUser<T>( String userId, T dataObject )
public void DenyForUser<T>( String userId, T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.DenyForUser( userId, dataObject );
DataPermission.UPDATE.DenyForUser( userId, dataObject );
DataPermission.REMOVE.DenyForUser( userId, dataObject );
where:
| Argument | Description |
|---|---|
userId |
A user ID, for which you want to revoke a permission. |
dataObject |
A data object for which you want to revoke the permission. |
Codeless Reference¶
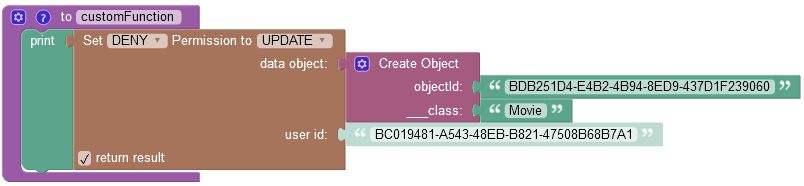
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to revoke from a user. |
data object |
A data object for which you want to revoke the permission. |
user id |
A user ID, for which you want to revoke a permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To deny access for a user role¶
//Signature
public void DenyForRole<T>( String roleName, T dataObject )
public void DenyForRole<T>( String roleName, T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.DenyForRole( roleName, dataObject );
DataPermission.UPDATE.DenyForRole( roleName, dataObject );
DataPermission.REMOVE.DenyForRole( roleName, dataObject );
where:
| Argument | Description |
|---|---|
roleName |
A role name, for which you want to revoke a permission. |
dataObject |
A data object for which you want to revoke the permission. |
Codeless Reference¶
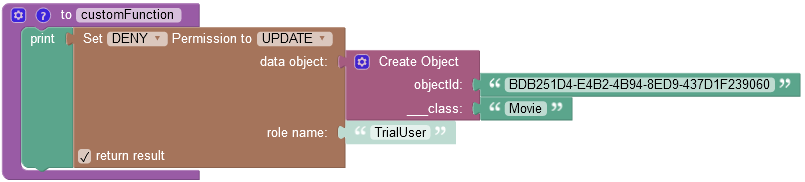
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to revoke from a role. |
data object |
A data object for which you want to revoke the permission. |
role name |
A role name, for which you want to revoke a permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To deny access for all users¶
//Signatures
public void DenyForAllUsers<T>( Object dataObject )
public void DenyForAllUsers<T>( T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.DenyForAllUsers( dataObject );
DataPermission.UPDATE.DenyForAllUsers( dataObject );
DataPermission.REMOVE.DenyForAllUsers( dataObject );
where:
| Argument | Description |
|---|---|
dataObject |
A data object for which you want to revoke the permission. |
Codeless Reference¶
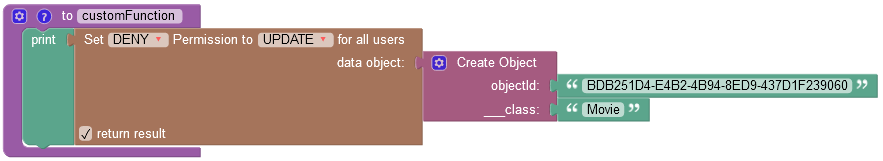
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to revoke from all users. |
data object |
A data object for which you want to revoke the permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |
To deny access for all user roles¶
//Signatures
public void DenyForAllRoles<T>( T dataObject )
public void DenyForAllRoles<T>( T dataObject, AsyncCallback<Object> responder )
//Invocation
DataPermission.FIND.DenyForAllRoles( dataObject );
DataPermission.UPDATE.DenyForAllRoles( dataObject );
DataPermission.REMOVE.DenyForAllRoles( dataObject );
where:
| Argument | Description |
|---|---|
dataObject |
A data object for which you want to revoke the permission. |
Codeless Reference¶
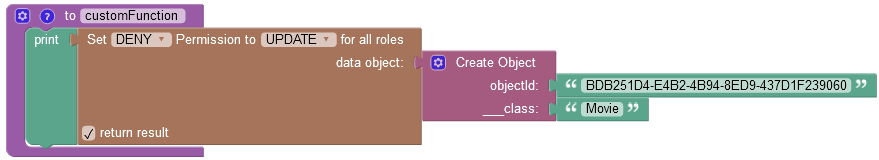
where:
| Argument | Description |
|---|---|
GRANT/DENY |
Specifies whether the permission must be granted or revoked. |
FIND/REMOVE/UPDATE |
Identifies the permission type to revoke from all roles. |
data object |
A data object for which you want to revoke the permission. |
return result |
When this checkbox is selected, the operation returns an empty string value. |
objectId |
Required property. Represents the unique identifier of the object in the data table. |
__class |
Required property. Represents the name of the data table where the operation takes place. |