OAuth1 Login API - Twitter¶
Description¶
The OAuth1 authorization protocol is only available for Twitter, use OAuth2 for other login providers.
This operation allows logging in the externally authenticated user to Backendless. It adds the Twitter's access token to BackendlessUser object and establishes the session. For more information see the Step 3 of the Login with Provider SDK flow.
Method¶
// Login for the OAuth1.0 provider (Twitter)
Backendless.UserService.loginWithOAuth1(
String providerCode,
String authToken,
String authTokenSecret,
Map<String, String> fieldsMappings,
AsyncCallback<BackendlessUser> responder,
boolean stayLoggedIn )
where:
| Argument | Description |
|---|---|
providerCode |
Name of the login provider as displayed in Backendless Console - see the specific provider screen at Users > Login Providers. String value. |
accessToken |
OAuth access token obtained from the authentication provider as a result of logging in the user. String value. |
accessTokenSecret |
Optional parameter. A unique value that should be obtained from the logic provider side. String value. |
fieldsMappings |
Optional parameter. A mapping of user properties between OAuth provider and Backendless. If the map object is not null, it should contain a mapping between the provider specific property names and the column names in the Users table. Consider the following mappings:"my_email" >> "email""my_name" >> "name"The key identifies the provider's property name and the value is the name of the mapped property (column name) in Backendless. In the example above, "my_email" and "my_name" are the properties returned by the OAuth1 provider and the corresponding values will be respectively stored in the "email" and "name" columns in Backendless. Must be an object. |
responder |
a responder object containing success/failure methods which are called when the user is logged in or if an error occurs. If the operation is successful, the responder method provides the BackendlessUser argument representing the currently logged in user. |
stayLoggedIn |
Optional parameter. Requests to store the user's login information so the login form can be skipped next time the user launches the app. Boolean value. |
guestUser |
Optional parameter. If present, must be the BackendlessUser object obtained through the Guest Login API. Must be an object. |
Return Value¶
The BackendlessUser object containing user data.
Example¶
The example below logs in the externally authenticated user ("twitter") to Backendless.
String authProviderCode = "twitter";
String authToken = "<authToken>";
String authTokenSecret = "<authTokenSecret>";
Map<String, String> fieldsMappings = new HashMap<>();
boolean stayLoggedIn = true; // or false
Backendless.UserService.loginWithOAuth1( authProviderCode, authToken, authTokenSecret, fieldsMappings, new AsyncCallback<BackendlessUser>()
{
@Override
public void handleResponse( BackendlessUser backendlessUser )
{
// result handling logic
}
@Override
public void handleFault( BackendlessFault backendlessFault )
{
// error handling logic
}
}, stayLoggedIn );
String authProviderCode = "twitter";
String authToken = "<authToken>";
String authTokenSecret = "<authTokenSecret>";
BackendlessUser guestUser = Backendless.UserService.loginAsGuest();
Map<String, String> fieldsMappings = new HashMap<>();
boolean stayLoggedIn = true; // or false
Backendless.UserService.loginWithOAuth1( authProviderCode, authToken, authTokenSecret, fieldsMappings, new AsyncCallback<BackendlessUser>()
{
@Override
public void handleResponse( BackendlessUser backendlessUser )
{
// result handling logic
}
@Override
public void handleFault( BackendlessFault backendlessFault )
{
// error handling logic
}
}, stayLoggedIn );
Codeless Reference¶
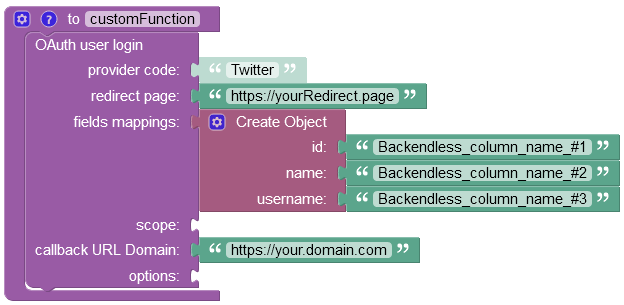
where:
| Argument | Description |
|---|---|
provider code |
Code of the login provider as displayed in Backendless Console - see the specific provider screen at Users > Login Providers. |
redirect page |
Optional parameter. You can set the redirect page or an absolute path to an .html file in your application storage ( e.g. /web/index.html) that a user will see after the authorization. |
fields mappings |
Optional parameter. A mapping of user properties between OAuth provider and Backendless. If the object is not null, it should contain a mapping between the provider specific property names and the column names in the Users table. Consider the following mappings:"my_email" >> "email""my_name" >> "name"The key identifies the provider's property name and the value is the name of the mapped property (column name) in Backendless. In the example above, "my_email" and "my_name" are the properties returned by the OAuth2 provider and the corresponding values will be respectively stored in the "email" and "name" columns in Backendless. |
scope |
Optional parameter. A collection of security scopes the client application is requesting permissions for. You must obtain security scopes from your Login Provider. Furthermore, you must pay attention how you pass data to this parameter, since all providers have different format of security scopes as well as separators. A separator can be a space, comma, ampersand or other symbol standardized by the Login Provider of your choice. |
callback URL Domain |
Optional parameter. A custom or Backendless domain used to retrieve the Login Provider's authorization token. Refer to the Login With Provider's SDK section in this topic, Step 2, to see the authorization process. |
options |
Optional parameter, which is used to pass the clientID for Apple authorization. |
Returns the BackendlessUser object containing user information for all the properties stored in the Backendless database.
The example below performs the authorization of a user using Twitter as the Login Provider.
For demonstration purposes the fields mappings parameter contains a sample object with field names that should match the field names as provided by your Login Provider; If fields are matched, then the user information is exchanged between the Backendless and the Login Provider, and saved to the Users data table.
There are no security scopes for Twitter Login API, since it is the OAuth1 login operation.
Refer to the Twitter developer documentation to learn more about the Twitter's user object.