Database Security Best Practices

Following the database security best practices outlined in this article will help ensure that your data is kept confidential and secure in the face of malicious attacks and data breaches.
Whether you are creating a database from scratch with code or working with one of the many no-code development tools, you to ensure the data you collect is protected. Databases range in size and complexity from small and simple to massive and complex, but no matter the size or structure, the data within must be secure.
Organizations are no longer obligated to own physical database servers. Cloud-based web servers, also known as serverless hosting, are becoming the standard for small and medium sized businesses to host their databases. Even many large organizations are moving in this direction. The reason for this is more than just monetary.
A crucial element that developers are paying for when utilizing web servers and cloud-based services is security. Or rather, maintaining database security without having to implement their own security systems.

This article will discuss best security practices for database servers, regardless of whether they are cloud servers or your own servers. We will cover the primary purposes of maintaining a secure database, but ultimately it boils down to two keys: protecting proprietary and user data, and avoiding data loss.
Database security components include tools, controls, and processes. Effective database security measures protect your database management system from unauthorized access, illegitimate use, and malicious cyberattacks by ensuring their confidentiality, integrity, and availability.
A database is more vulnerable to threats if it is easier to access and use. Once security measures are increased, the threat resistance of the database increases. However, accessing and using the database becomes more difficult. For a database management system provider like Backendless, the priority is striking the right balance between ease of use and security.
Benefits of Maintaining Database Security
It seems every week a news story breaks of a major data breach involving a massive corporation. In many instances, a enormous amount of information is stolen due to a relatively small gap in security. In 2021 and beyond, maintaining a proactive approach to database security will reap the many benefits.
a) Protecting Data Is Protecting Assets
First and foremost, there is no such thing as a small database breach. Threat actors can wreak havoc on a database whether they are insider threats or external threats that gain access to your network.
In an increasingly digital world, the value of data is only going to continue to increase. Data enables many systems that today’s businesses rely on, such as personalized digital experiences and just-in-time inventory and logistics systems. Valuable data that’s lost or compromised can have wide-ranging effects on a business.
Internally, information security plays an important role in ensuring your database’s reliability. If your database is experiences data loss or disruptions, the value of that information diminishes greatly.
b) Having fewer errors increases the security of data
Automating and securing databases go hand in hand. You can identify and mitigate security threats in real time using machine learning technology and automated detection. You are less likely to get false positives and more likely to be able to stop cyberattacks in time with faster insights and more accurate monitoring.
c) Build relationships with customers
The concept of data privacy extends far beyond the simple act of ticking boxes. It’s not the easiest task for consumers to decide what information to share and with whom. In today’s world, if a customer does not trust you with their data, there’s a good chance they won’t spend their money with your business, period.
Lost or compromised customer data is a public relations nightmare. A data breach erodes customer trust in the organization, even if the organization is not a digital-first business.
d) Ensure Data Security for Your Brand
While we live in a data-driven age, the customer still reigns supreme. Getting your customers’ trust back is difficult when you’ve lost it. Data breaches caused by companies will never cause consumers to do business with them again, according to Secure Link.
Your customers need to be confident in their sensitive data’s safety. The loss of trust from a breach can cause customers to run to your competitors, while the gain of trust can make them loyal to you.
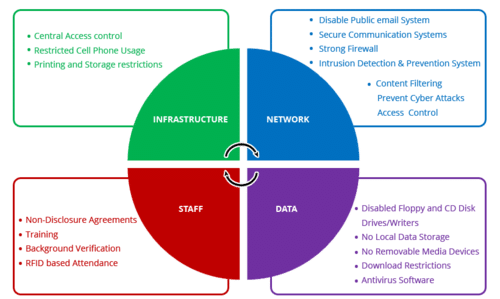
Top 8 Database Security Best Practices
Approximately 36 billion records were compromised between January and September 2020, according to Risk Based Security’s 2020 Q3 report. In addition to being staggering, this result emphasizes the need for security controls of database server infrastructure.
There are some differences between database security and website security. Best practices for database security require physical security steps and sometimes even software solutions. Cyber criminals can use a wide range of attack vectors to penetrate your site, so it’s also important to protect your site from them.
We will cover several database security best practices in this article, which will help keep your databases safe from attacks. If you are looking to host your own data, these steps can act as a basic database security plan to get you started.
1. Ensure that the physical databases are secure
A web hosting company with a history of taking security matters seriously should be considered when choosing a web hosting service. A free hosting service may be insecure, so it’s typically best to avoid them.
You should make sure your servers are physically secure by adding surveillance cameras, locks, and staff security. To reduce the risk of malicious activities, all physical server access should be logged and only given to the appropriate people.
If you are planning to use web servers, you will want to research the hosting company to ensure there are no red flags related to previous breaches or data loss.
2. Separate database servers
To keep databases safe from cyberattacks, specialized security measures must be taken. Storing your data on the same server as your website also exposes your data to different attack vectors that target your site.
Your database servers should be isolated from everything else in order to reduce these security risks. Security information and event management (SIEM) provides organizations with real-time access to relevant information to enable them to respond more quickly to attempted breaches.
3. Install a proxy server that provides HTTPS access
When a workstation requests a database server, a proxy server examines the request. In this server, also known as a database server firewall, unauthorized users are prevented from accessing the database.
HTTP proxy servers are the most common type of proxy server. Whenever your organization is handling sensitive data, such as credit card information, payment details, or personal information, you need an HTTPS server. Consequently, the proxy server also encrypts any data traveling through it, adding another layer of security.
4. Implement an encryption protocol
You shouldn’t just encrypt your data when keeping trade secrets; you should also encrypt sensitive user information when transferring or storing it.
By using encryption protocols, data breaches are less likely to happen. Cybercriminals are therefore unable to access your data even if they get their hands on it.
5. Ensure your database is regularly backed up
Backing up your website is common practice, but you should also regularly back up your database. Thus, a malicious attack or data corruption cannot lead to the loss of sensitive information.

Using Windows or Linux, here is how to back up a database. In addition to storing the backup on a separate server, improve security by encrypting it there as well. By using a backup database server, your data is secure even if your primary server gets compromised or is not accessible.
6. Update applications on a regular basis
There are outdated software components in nine of ten applications. In addition, an analysis of WordPress plugins revealed 17,383 plugins were not updated for two years, 13,655 plugins were not updated for three years, and 3,990 plugins were not updated for seven years. Using outdated software to maintain databases or even to run a website can create a serious security risk as a result of this problem.
Database security management software should only be used by trusted and verified vendors, and it should be kept updated and patches added when they are released. In addition, widgets, plugins, and third-party applications shouldn’t be used if they haven’t been regularly updated.
7. Authenticate users strongly
You can also add an additional layer of security to your database if you implement multi-factor authentication. Cyber criminals might have difficulty circumventing this security method even if credentials get compromised, although it isn’t perfect because of recent trends. To further reduce the risk of a security breach, consider allowing the database to only be accessed from validated IP addresses. It is possible to copy or mask IP addresses, but the attacker must put in more effort.
8. Assign all users security roles
Finally, we want to touch on an approach taken by Backendless to ensure database security for all of our users. Roles-based security is a relatively simple but highly effective approach to limiting data access. This practice is particularly valuable for organizations that make their database available to outside parties or customers via API services.
Every attempt to access a Backendless database by API requires security authentication. If no authentication is provided, the party attempting to access the database is treated as a guest or nonauthenticated user, and their access to the database as well as ability to make modifications are severely limited. This approach ensures a high level of database confidentiality.
Conclusion
Backendless provides secure serverless hosting, meaning we offer database security so you don’t have to worry about. We also, however, offer limitless Backendless Pro and Managed Backendless products that can be hosted on your own servers, meaning you will be responsible for protecting your database servers.
You can develop a more robust security framework to protect your data, servers, and users’ sensitive information by implementing some of the database best security practices in this post. In the end, the better you are at preventing attacks and protecting sensitive data, the better chance your organization will have of building long-term customer relationships and maintaining sustainable business partnerships.
References
Bertino, E., & Sandhu, R. (2005). Database security-concepts, approaches, and challenges. IEEE Transactions on Dependable and secure computing, 2(1), 2-19.
Paul, P., & Aithal, P. S. (2019). Database Security: An Overview and Analysis of Current Trend. International Journal of Management, Technology, and Social Sciences (IJMTS), 4(2), 53-58.
Toapanta, S. M., Quimis, O. A. E., Gallegos, L. E. M., & Arellano, M. R. M. (2020). Analysis for the evaluation and security management of a database in a public organization to mitigate cyber-attacks. IEEE Access, 8, 169367-169384.
Gertz, M., & Jajodia, S. (Eds.). (2007). Handbook of database security: applications and trends. Springer Science & Business Media.