Phishing attack
This morning we got an alert from Google saying that some phishing content had been detected in Backendless. Indeed, a user created an app in Backendless and uploaded a phishing page to the Backendless File storage.
Static content from the file storage in Backendless is served via the backendlessappcontent.com domain. Since the domain (from the Google’s perspective) is associated with the phishing content, any file served from the domain is now preceded with the following screen in Chrome:
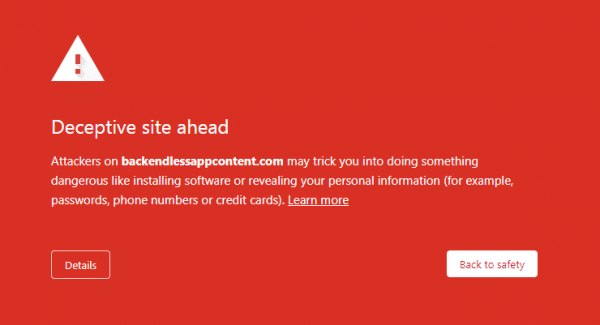
What has been done to remove the warning?
Once we learned about the problem, we immediately deleted the application with the phishing content and blocked the developer’s account. We notified Google about the changes on our site and once they verify them, the domain will be cleared from the “deceptive sites” list.
What can you do to avoid the error?
The best way to ensure your application is not impacted by this problem is by adding a custom domain to your application. A custom domain can be registered in Backendless console. You can find the instructions in our documentation. Once a custom domain is deployed, files in your Backendless file storage can be accessed through your own custom domain.
How can I bypass the warning in Chrome?
To bypass the warning, click the “Details” button and click the “visit this unsafe site” link.
Is Backendless unsafe?
While the warning in Chrome’s says so, we believe Backendless is safe. Google doesn’t know what backendlessappcontent.com is used for and how it works. The phishing content deployed in one app (which now has been deleted) has no impact on the files in your app. Unfortunately, this is a good example of when one bad apple can spoil the bunch.