Asset Permissions¶
Asset permissions are the most granular in the Backendless security system as they apply to a specific object. Currently this type of permissions is available only for data objects stored in Backendless Data Service and files stored in Backendless File Service. Permissions assigned to an asset (data objects or files) supersede all other permissions - including global and asset container ones.
Similar to the asset container permissions, asset permissions may apply to specific user accounts or roles. This approach becomes particularly useful when different objects/files in the same container (table or directory) should have different access levels. For example, suppose a data table called Orders contains purchase orders entered by different sales people. Every sales person should be able to see only their purchase orders, but the sales manager should see the purchase orders of his subordinates. This can be accomplished by using an asset permission scheme.
Data Service Asset Permissions¶
Permissions for individual data objects can be managed either with Backendless Console or using the API. To manage object's permissions with console:
- Login to console and select an application.
- Click Data, then select the table containing the object for which permissions should be managed.
- There is a special "lock" icon in the ACL column for every object in the table.
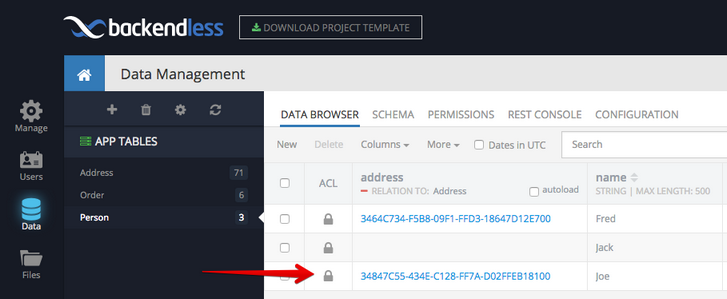
- Click the lock icon to manage object's permissions.
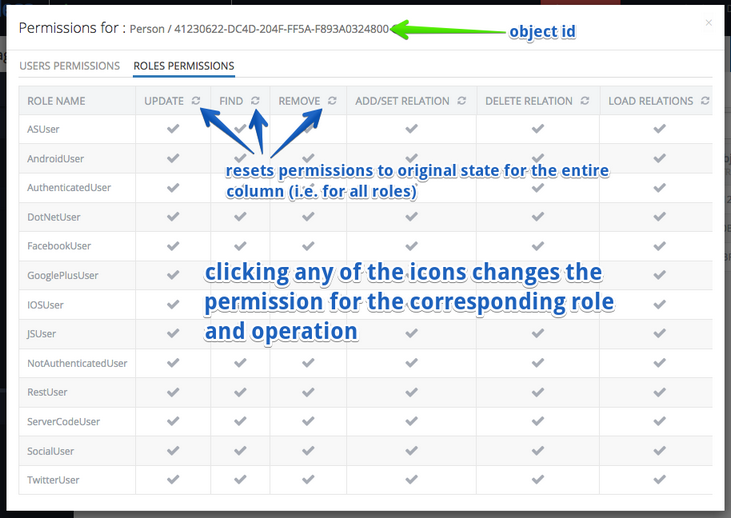
- The permissions user interface includes two menu items: Users Permissions and Roles Permissions. The former is responsible for assigning permissions for the selected object to specific users. The latter does the same but for application roles.
The screenshot below explains various parts of the user interface:
The intersection of each column and a role/user either grants or denies access to the operations represented by the column. The intersections may contain the following visualizations:
| Visualization |
Access |
Description |
|---|---|---|
 (gray check mark) (gray check mark) |
INHERIT |
This state represents the permissions for the user/role and the operation are inherited from either asset container or global permissions. |
 (green check mark) (green check mark) |
GRANT |
This state represents that the permission is granted for the user/role to perform the corresponding operation. |
 (red cross) (red cross) |
DENY |
This state represents that the permission to execute the corresponding operation is denied to the user/role. |