Backendless provides bulletproof security with a model accommodating virtually all application needs. The model is based on a mapping between an API operation performed by your app and a security “principal”, which is either a role or a user. When configuring your security policy with our graphical interface, you do not need to write any code or know any proprietary security configuration formats. A policy configuration is a set of permissions you create between your data and users and the Backendless APIs connecting the two. The system supports a tiered approach, allowing you to set both broad and specific security rules. Security configuration works the same way for files, messaging channels, geolocation storage, and the database as a whole.
Security
At A Glance

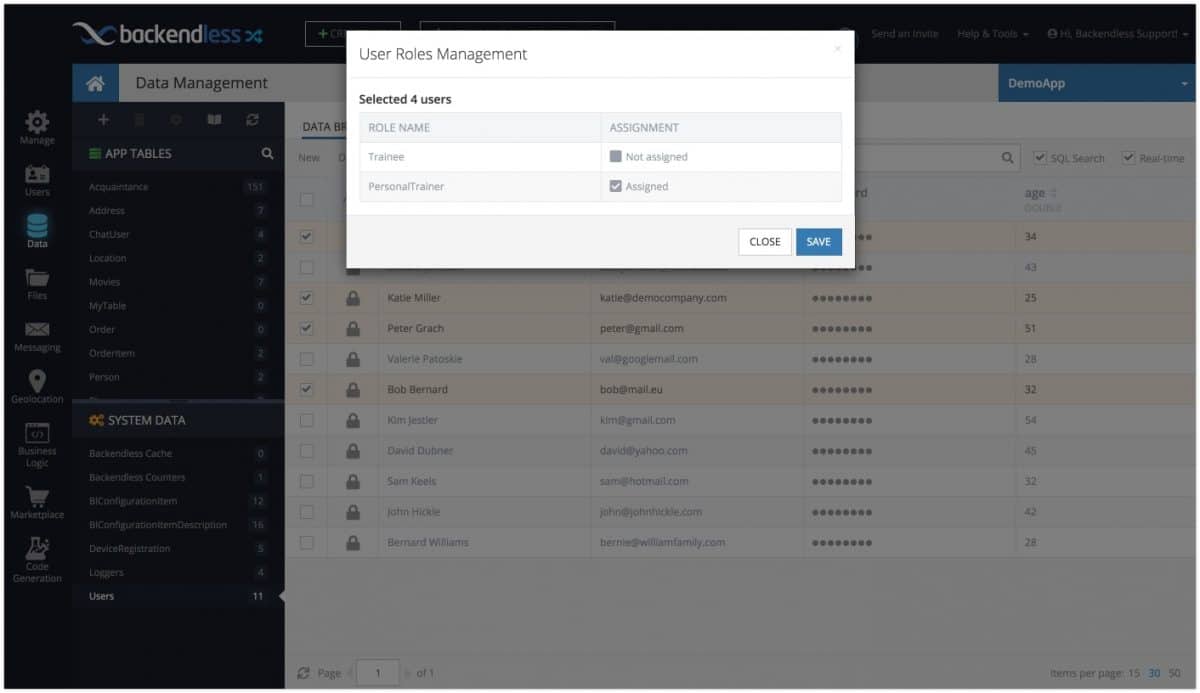
Roles-Based Policies
Backendless supports two types of roles: built-in (system) roles and custom (developer-defined) roles. API requests made by your app are always linked to the identity of the user making the request. When a user is logged into your app, that user’s identity is assigned to each API call made by the application. Every user in your app is assigned one or more built-in and/or custom roles. Backendless assigns security roles based on the user’s identity to every single API request. The assigned roles are a combination of the user’s system and custom roles. Every single role has a set of permissions for every API. You can adjust the permissions to specify which APIs each of the roles can access.

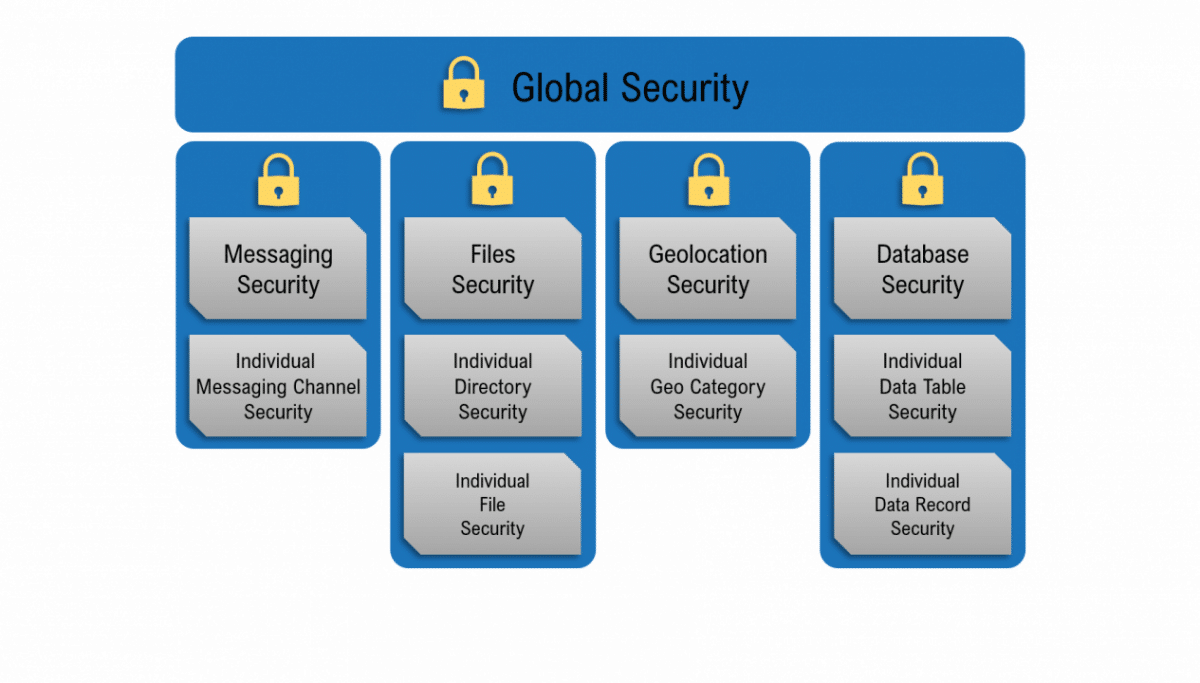
Multi-Tier Model
Both system and custom security roles have permissions defined at different levels (tiers) of your backend. These levels include the global level, the data table level, and the individual object level. An individual database table may have its own set of permissions for the same roles. Each individual object in a data table may also have its own permissions for each role. In order for Backendless to make the decision whether an API request should be rejected or not due to security permissions, it checks each tier in accordance with the rules of the security hierarchy.

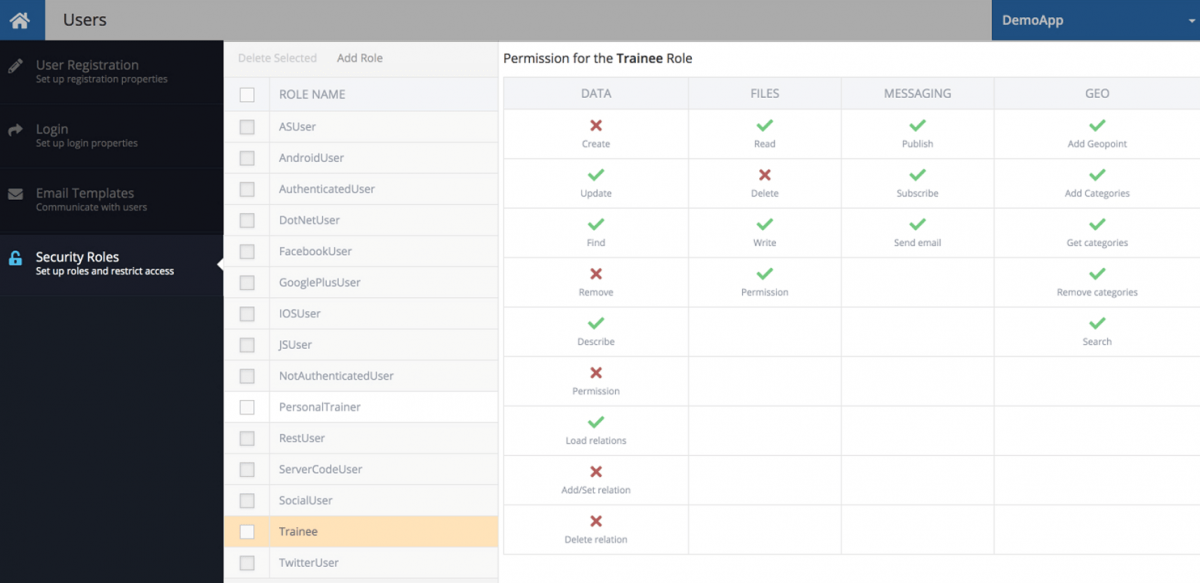
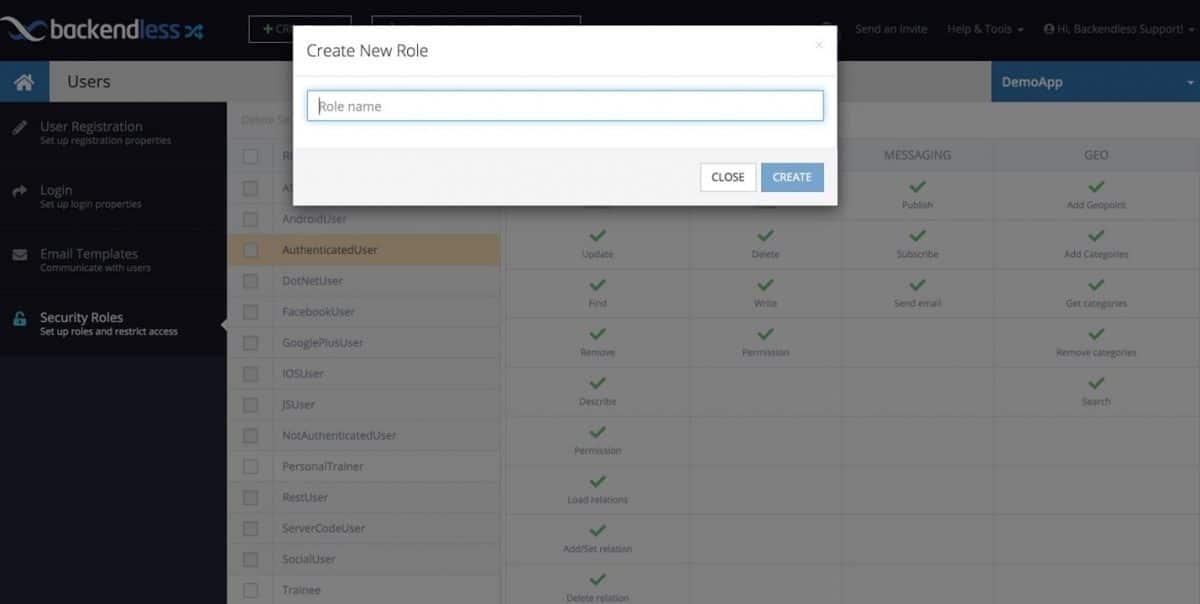
Visual Policy Management
Configuring your security policy in Backendless can be done visually in Backendless Console. You do not need to learn any specialized or proprietary syntax for declaring security permissions for your app’s backend. Restricting access to data or APIs is as simple as point-and-click. Permission statuses are represented through common icons, such as:
- [green check] permission granted
- [red X] permission denied
- [grey check] granted permission inherited

Global Tier
You can assign global permissions to any system or custom role. These permissions apply globally to all tables in the database, all directories in the file storage, all geo categories and messaging channels. Permission assignments you add at lower levels take priority over global settings. This approach makes it convenient to establish a global security policy for an app while still having the ability to lock or unlock specific tables and objects as needed. For example, you may want to restrict access for non-authenticated users to all but a small subsection of your database.

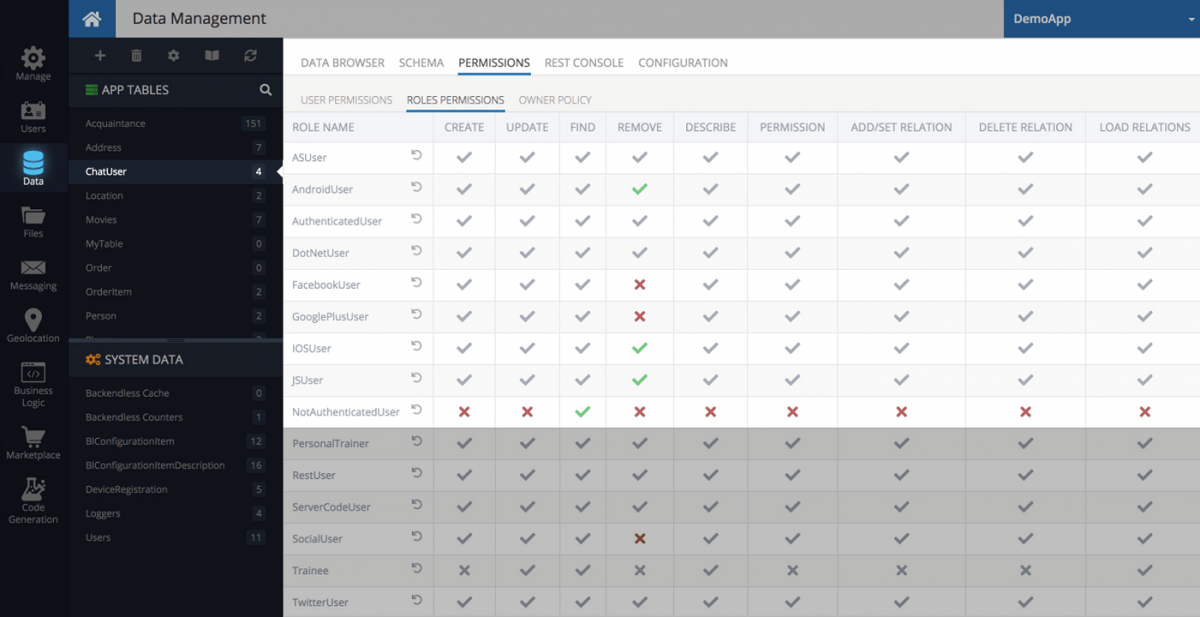
Database Tier
Access to data and Database APIs can be restricted at the individual table level/tier. Table level permissions can be assigned for both user roles and individual user accounts. Permissions assigned at the table level override those at the global tier. That means if a role is denied access globally, you can override it for a specific table.

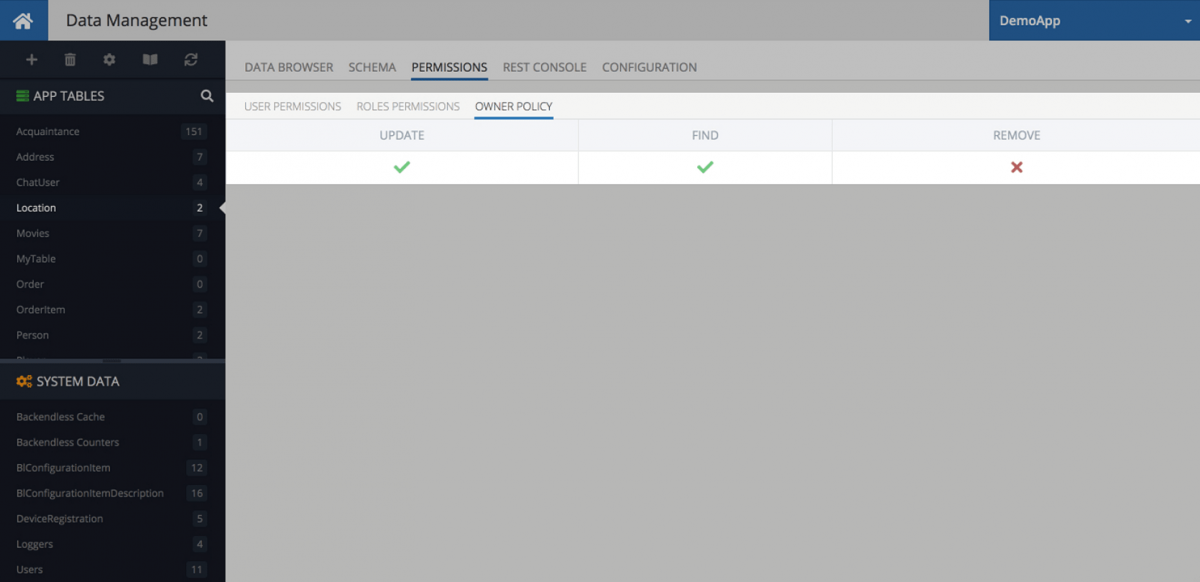
Owner Policy
For many apps, it is important to limit the user’s access to only the data that “belongs” to them. For example, a To-Do List app might let a user manage only the tasks created by them. Backendless makes it very easy to configure permissions to where the database only returns the objects associated with the currently logged-in user. This is made possible through Owner Policy. You don’t need to write any additional code to enable this type of data retrieval – Backendless handles it completely automatically.

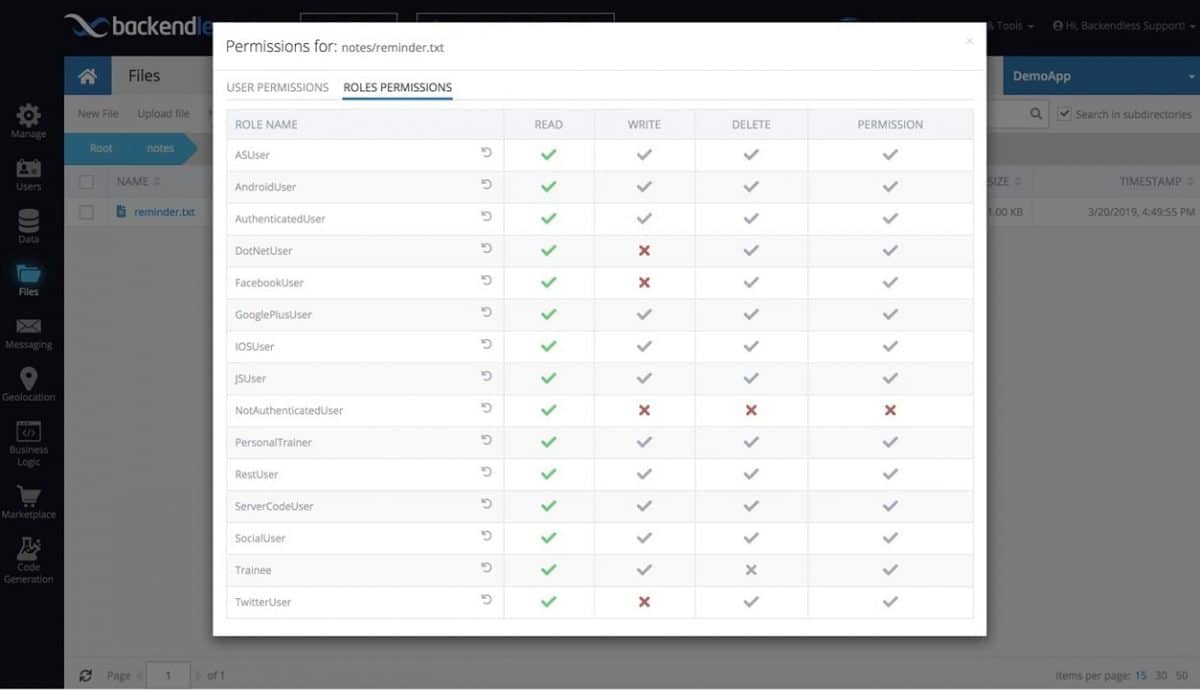
Files Security
Access to Backendless File Storage can be restricted for security roles or individual users. You can set permissions for API operations for uploading, retrieving or deleting files. These permissions can be applied at the global tier or assigned to individual directories or files.

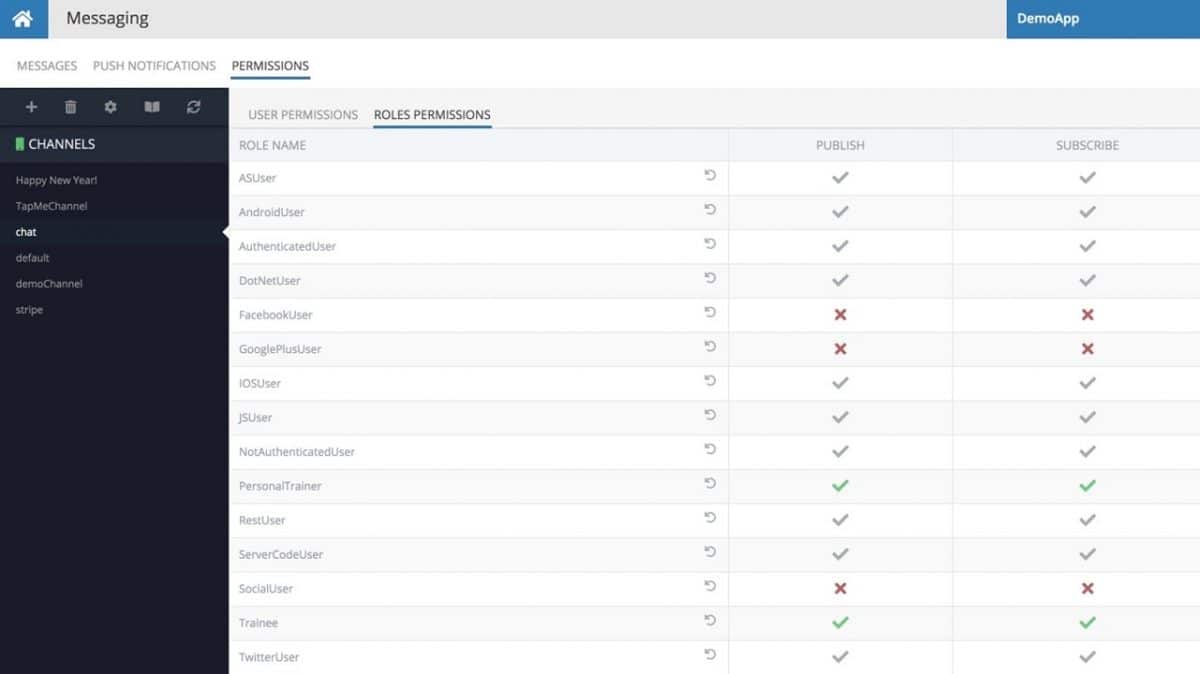
Messaging Security
Both message publishing and subscription APIs are subject to security restrictions. You can decide which users or security roles can perform the functions of sending out messages, publishing push notifications, and subscribing to receive them. You can set different security restrictions for these operations for each channel.

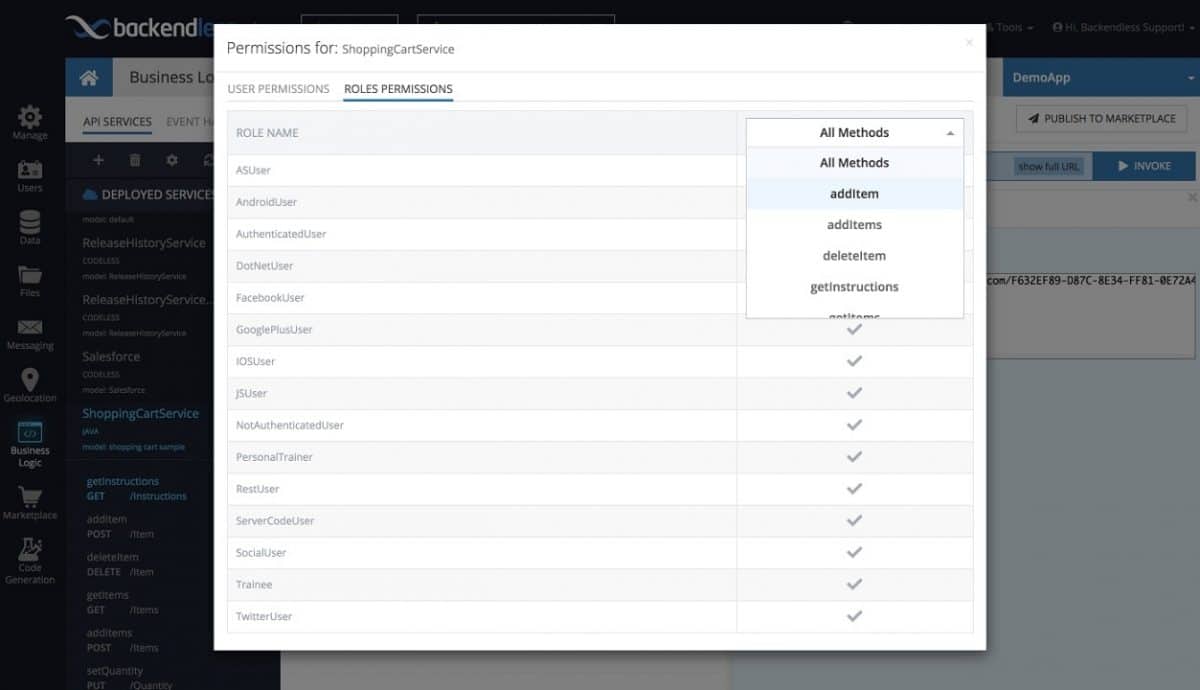
API Services Security
Access to your custom API services can be restricted in the same way that access to Backendless’ built-in APIs can. You can restrict access to specific users or any system and/or custom security roles. You can also configure access at the operations (methods/functions) level, which means you can grant access to a specific operation for one role and deny it for another role. When access is denied for a role, any user assigned that role will receive a security error when trying to invoke the API service.
