Service Security¶
Access to service APIs can be restricted with the user/role-based security of the application where the service runs. A permission either allows or denies invocation of a method for a specific user or all users who belong to a role. Follow the steps below to configure service security:
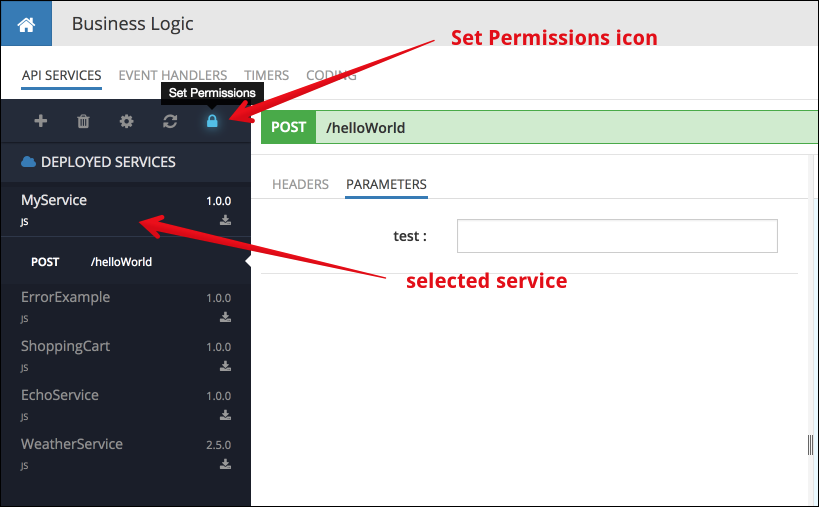
- Login to Backendless console, select the application where the service is deployed and click the Business Logic icon.
- Select a service from the list in the API Services section.
- Click the Set Permissions icon in the toolbar:
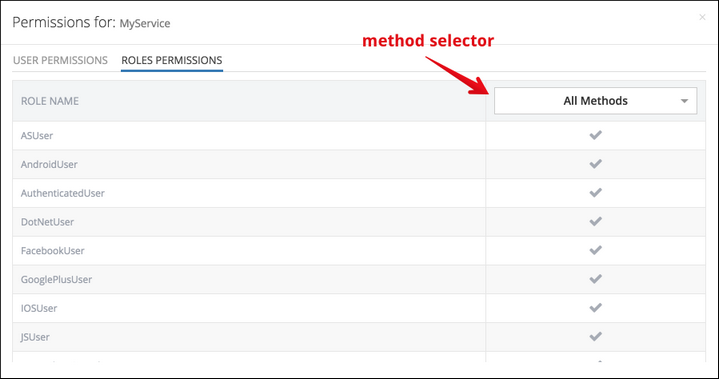
The permissions management user interface has two sections: User Permissions and Roles Permissions. Both sections use the same principle for applying permissions to users/roles for all or specific service methods. Select a method which should be secured using the method selector list or if the permission assignment for a user/role is going to be the same for all methods, use All Methods:
To change permission assignment, click the icon at the intersection of a user/role row and the Method column. The icon represents the current permission and has three states which can be changes by clicking the icon.
 - Represents a permission allowing method invocation for the specified user or role.
- Represents a permission allowing method invocation for the specified user or role.
 - Represents a permission denying method invocation for the specified user or role.
- Represents a permission denying method invocation for the specified user or role.
 - Represents "inherited" permission allowing method invocation. Since service permissions do not have the concept of global assignments, the gray check mark essentially is the same as the green one.
- Represents "inherited" permission allowing method invocation. Since service permissions do not have the concept of global assignments, the gray check mark essentially is the same as the green one.
Runtime Permission Handling¶
The NotAuthenticatedUser role applies to any API request which does not have a user identity identified by the user-token HTTP header. The value of the user-token header is obtained on the client side from the result of the login API.
When Backendless receives a service API call, it uses the value from the user-token header to determine the user's identity and all the roles the user belongs to. Once a list of roles is identified, Backendless checks all assigned permissions for the user and his roles for the invoked method. If any of the permissions deny access, the invocation will be denied and an error is returned back to the client.
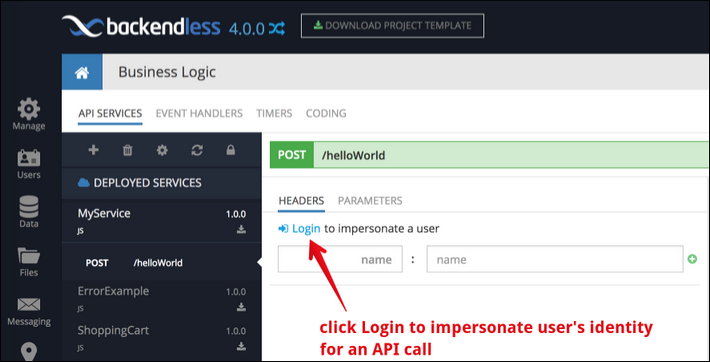
When testing service invocations with Backendless console, an authenticated request can be performed by logging in a user on the HEADERS page for a method:
Once a user is logged in, Console uses the assigned user-token for all service method invocations made through console.